June/2023 Latest Braindump2go AZ-801 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go AZ-801 Real Exam Questions!
QUESTION 89
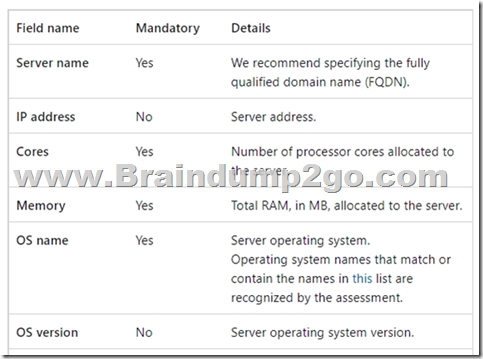
You need to use a comma-separated value (CSV) file to import server inventory to Azure Migrate.
Which fields are mandatory for each entry in the CSV file?
A. Server name, Cores, OS Name, and Memory (in MB)
B. Server name, IP addresses, Disk 1 size (in GB), and CPU utilization percentage
C. Server name, IP addresses, OS version, and Number of disks
Answer: A
Explanation:
The following table summarizes the file fields to fill in:
Reference:
https://docs.microsoft.com/en-us/azure/migrate/tutorial-discover-import
QUESTION 90
Your on-premises network has a 200-Mbps connection to Azure and contains a server named Server1 that stores 70 TB of data files.
You have an Azure Storage account named storage 1.
You plan to migrate the data files from Server1 to a blob storage container in storage!. Testing shows that copying the data files by using azcopy will take approximately 35 days.
You need to minimize how long it will take to migrate the data to Azure.
What should you use?
A. Storage Migration Service
B. Azure Storage Explorer
C. Azure Data Box
D. Azure File Sync
Answer: C
Explanation:
The Microsoft Azure Data Box cloud solution lets you send terabytes of data into and out of Azure in a quick, inexpensive, and reliable way. The secure data transfer is accelerated by shipping you a proprietary Data Box storage device. Each storage device has a maximum usable storage capacity of 80 TB and is transported to your datacenter through a regional carrier. The device has a rugged casing to protect and secure data during the transit.
Reference:
https://docs.microsoft.com/en-us/azure/databox/data-box-overview
QUESTION 91
You have an Azure virtual machine named VM1 that runs Windows Server.
When you attempt to install the Azure Performance Diagnostics extension on VM I, the installation fails.
You need to identify the cause of the installation failure.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Sign in to VM1 and verify the WaAppAgent.log file.
B. From the Azure portal, view the alerts for VM1.
C. From the Azure portal, view the activity log for VM1.
D. Sign in to VM1 and verify the MonitoringAgent.log file.
Answer: AC
Explanation:
Windows Azure Guest Agent Service: This service is the service that is responsible for all the logging in WAppAgent.log. This service is responsible for configuring various extensions and communication from Guest to Host.
Activity log: See activity log entries filtered for the current virtual machine. Use this log to view the recent activity of the machine, such as any configuration changes and when it was stopped and started.
Reference:
https://docs.microsoft.com/en-us/troubleshoot/azure/virtual-machines/performance-diagnostics-vm-extension
https://docs.microsoft.com/en-us/azure/azure-monitor/vm/monitor-virtual-machine-analyze
QUESTION 92
Your network contains an Active Directory Domain Services (AD DS> domain. The domain contains 20 Active Directory sites. All user management is performed from a central site.
You add users to a group.
You discover that group changes do NOT appear on a domain controller in a remote site.
You need to identify whether the group changes appear on other domain controllers.
What should you use?
A. Microsoft Support and Recovery Assistant
B. File Replication Service (FRS) Status Viewer
C. Active Directory Replication Status Tool
D. Active Directory Sites and Services
Answer: C
Explanation:
The Active Directory Replication Status Tool (ADREPLSTATUS) analyzes the replication status for domain controllers in an Active Directory domain or forest.
The Active Directory Replication Status Tool (ADREPLSTATUS) analyzes the replication status for domain controllers in an Active Directory domain or forest.
ADREPLSTATUS displays data in a format that is similar to REPADMIN /SHOWREPL * /CSV imported into Excel but with significant enhancements.
Specific capabilities for this tool include:
– Expose Active Directory replication errors occurring in a domain or forest
– Prioritize errors that need to be resolved in order to avoid the creation of lingering objects in Active Directory forests
– Help administrators and support professionals resolve replication errors by linking to Active Directory replication troubleshooting content on Microsoft TechNet
– Allow replication data to be exported to source or destination domain administrators or support professionals for offline analysis
Reference:
https://www.microsoft.com/en-us/download/details.aspx
QUESTION 93
You have five Azure virtual machines. You have a dedicated Azure Storage account to collect performance data.
You need to send the collected data directly to the Azure Storage account.
What should you install on the virtual machines?
A. the Telegraf agent
B. the Azure Monitor agent
C. the Dependency agent
D. the Azure Diagnostics extension
E. the Azure Connected Machine agent
Answer: D
Explanation:
Diagnostic extension is required to send data directly to Azure Storage.
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/diagnostics-extension-overview
QUESTION 94
You have three servers named Server 1. Servers and Server3 that run Windows Server. The servers have the Hyper-V server rote installed and are configured in a Storage Spaces Deed cluster named Cluster1.
Cluster1 hosts a virtual machine named VM1 that has Windows Admin Center Installed.
You manage all servers and clusters by using Windows Admin Center.
You purchase an Azure subscription.
You need to configure email alerts in Azure Monitor for the following:
– Disk Capacity Utilization Over 80% for 10 Minutes
– Any critical alert in the cluster system event log
– Memory Utilization over 95% for 10 minutes
– Heartbeat fewer than 5 beats for 5 Minutes.
– CPU Utilization over 85 % for 10 Minutes.
– Any hearth service faults for the cluster
The solution must use the minimum amount of administrative effort.
What should you do?
A. From Windows Admin Center, configure Azure Monitor and onboard Cluster1.
B. From the Azure portal, configure Azure Monitor and onboard Cluster1 by using Azure Arc.
C. Configure Azure Monitor and manually install the Microsoft Monitoring Agent on Server1 Server2, and Server3.
Answer: A
Explanation:
https://learn.microsoft.com/en-us/windows-server/storage/storage-spaces/configure-azure-monitor
QUESTION 95
You have a three-node failover cluster.
You need to run pre-scripts and post-scripts when Cluster-Aware Updating (CAU) runs. The solution must minimize administrative effort.
What should you use?
A. Scheduled tasks
B. Run profiles
C. Azure Functions
D. Windows Server Update Serveries (WSUS)
Answer: B
Explanation:
Cluster-Aware Updating advanced options and updating run profiles.
You can set the PreUpdateScript or PostUpdateScript the option.
Reference:
https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating-options
QUESTION 96
You have two Azure Virtual machines that run Windows Server.
You plan to create a failover cluster that will host the virtual machines.
You need to configure an Azure Storage account that will be used by the cluster as a cloud witness.
The solution must maximize resiliency.
Which type of redundancy should you configure for the storage account?
A. Geo-zone-redundant storage (GZRS)
B. Geo-redundant storage (GRS)
C. Zone-redundant storage (ZRS)
D. Locally-redundant storage (LRS)
Answer: C
Explanation:
For Replication, you can select Locally-redundant storage (LRS) or Zone-redundant storage (ZRS) as applicable. ZRS offers more redundancy.
Reference:
https://docs.microsoft.com/en-us/windows-server/failover-clustering/deploy-cloud-witness
QUESTION 97
Your company uses Storage Spaces Direct.
You need to view the available storage in a Storage Space Direct storage pool.
What should you use?
A. The Get-StoragefileServer cmdlet
B. Resource Monitor
C. System Configuration
D. Windows Admin Center
Answer: D
QUESTION 98
Hotspot Question
You have an on-premises server named Server1 and a Microsoft Sentinel instance.
You plan to collect Windows Defender Firewall events from Server1 and analyze the event data by using Microsoft Sentinel.
What should you install on Server1, and which information should you provide during the installation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
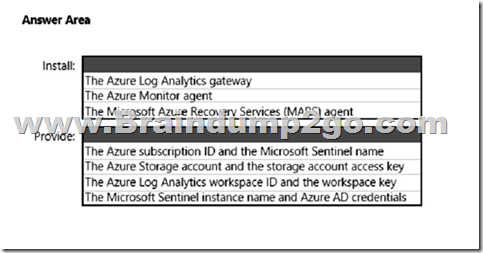
Answer:
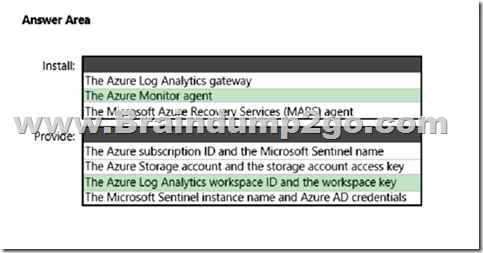
Explanation:
Box 1: Azure Monitor agent
The Azure Monitor agent supports Log Analytics, Metrics explorer, and Microsoft Sentinel.
Note: The Azure Monitor agent is meant to replace the Log Analytics agent, Azure Diagnostic extension and Telegraf agent for both Windows and Linux machines. It can send data to both Azure Monitor Logs and Azure Monitor Metrics and uses Data Collection Rules (DCR) which provide a more scalable method of configuring data collection and destinations for each agent.
Use the Azure Monitor agent if you need to:
* Collect guest logs and metrics from any machine in Azure, in other clouds, or on-premises. (Azure Arc-enabled servers required for machines outside of Azure.)
* Manage data collection configuration centrally, using data collection rules and use Azure Resource Manager (ARM) templates or policies for management overall.
* Send data to Azure Monitor Logs and Azure Monitor Metrics (preview) for analysis with Azure Monitor.
* Use Windows event filtering or multi-homing for logs on Windows and Linux.
Box 2: The Azure Log Analytics workspace ID and workspace key
The Azure Monitor agent sends data to Azure Monitor Metrics (preview) or a Log Analytics workspace supporting Azure Monitor Logs.
Enable Microsoft Defender for Cloud monitoring of on-premises Windows computers.
1. In the Azure portal on the Defender for Cloud – Overview blade, select the Get Started tab.
2. Select Configure under Add new non-Azure computers. A list of your Log Analytics workspaces displays, and should include the Defender for Cloud-
SentinelWorkspace.
3. Select this workspace. The Direct Agent blade opens with a link for downloading a Windows agent and keys for your workspace identification (ID) to use when you configure the agent.
4. Select the Download Windows Agent link applicable to your computer processor type to download the setup file.
5. To the right of Workspace ID, select Copy, and then paste the ID into Notepad.
6. To the right of Primary Key, select Copy, and then paste the key into Notepad.
Reference:
https://docs.microsoft.com/en-us/azure/architecture/hybrid/hybrid-security-monitoring
https://docs.microsoft.com/en-us/azure/azure-monitor/agents/agents-overview
QUESTION 99
Your network contains an Active Directory Domain Services (AD DS) domain named contoso.com. The domain contains three domain controllers named DC1, DC2, and DC3.
You connect a Microsoft Defender for Identity instance to the domain.
You need to onboard all the domain controllers to Defender for Identity.
What should you run on the domain controllers?
A. AzureConnectedMachineAgent.msi
B. MARAgentInstaller,exe
C. Azure ATP Sensor setup,exe
D. MMASetup-AMD64.exe
Answer: C
Explanation:
Azure ATP uses data from sensors, known as Azure ATP Sensors, that are installed on your domain controllers. The ATP sensors monitor the domain controller network traffic for signs of malicious activity, as well as other security risks such as connections made with weak or insecure protocols.
QUESTION 100
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a server named Server1 that runs Windows Server.
You need to ensure that only specific applications can modify the data in protected folders on Server1.
Solution: From App & browser control, you configure the Reputation-based protection.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 101
You deploy Azure Migrate to an on-premises network.
You have an on-premises physical server named Server1 that runs Windows Server and has the following configuration.
* Operating system disk 600 GB
* Data disic 3 TB
* NIC Teaming: Enabled
* Mobility service: installed
* Windows Firewall: Enabled
* Microsoft Defender Antivirus: Enabled
You need to ensure that you can use Azure Migrate to migrate Server1.
Solution: You disable Microsoft Defender Antivirus on Server1.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 102
You deploy Azure Migrate to an on-premises network.
You have an on-premises physical server named Server1 that runs Windows Server and has the following configuration.
* Operating system disk 600 GB
* Data disic 3 TB
* NIC Teaming: Enabled
* Mobility service: installed
* Windows Firewall: Enabled
* Microsoft Defender Antivirus: Enabled
You need to ensure that you can use Azure Migrate to migrate Server1.
Solution: You disable Windows Firewall on Server1.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 103
You deploy Azure Migrate to an on-premises network.
You have an on-premises physical server named Server1 that runs Windows Server and has the following configuration.
* Operating system disk 600 GB
* Data disic 3 TB
* NIC Teaming: Enabled
* Mobility service: installed
* Windows Firewall: Enabled
* Microsoft Defender Antivirus: Enabled
You need to ensure that you can use Azure Migrate to migrate Server1.
Solution: You shrink the data disk on Server1.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 104
You have three servers named Server1, Server2, and Server3 that run Windows Server and have the Hyper-V server role installed. Server1 hosts an Azure
Migrate appliance named Migrate1.
You plan to migrate virtual machines to Azure.
You need to ensure that any new virtual machines created on Server1, Server2, and Server3 are available in Azure Migrate.
What should you do?
A. On Migrate1, add a discovery source.
B. On the DNS server used by Migrate 1, create a GlobalName zone.
C. On Migrate1, set the Startup Type of the Computer Browser service to Automatic
D. On the network that has Migrate1 deployed, deploy a WINS server.
Answer: A
QUESTION 105
Your network contains an Active Directory Domain Services (AD DS) domain. All domain members have Microsoft Defender Credential Guard with UEFI lock configured.
In the domain, you deploy a server named Server1 that runs Windows Server. You disable Credential Guard on Server1.
You need to ensure that Server1 is NOT subject to Credential Guard restrictions.
What should you do next?
A. Run the Device Guard and Credential Guard hardware readiness tool.
B. Disable the Turn on Virtualization Based Security group policy setting.
C. Run dism and specify the /Disable-Feature and /FeatureName:IsolatedUserMode parameters.
Answer: B
QUESTION 106
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
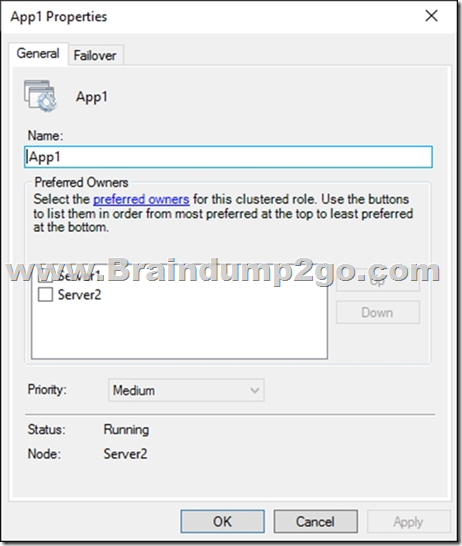
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
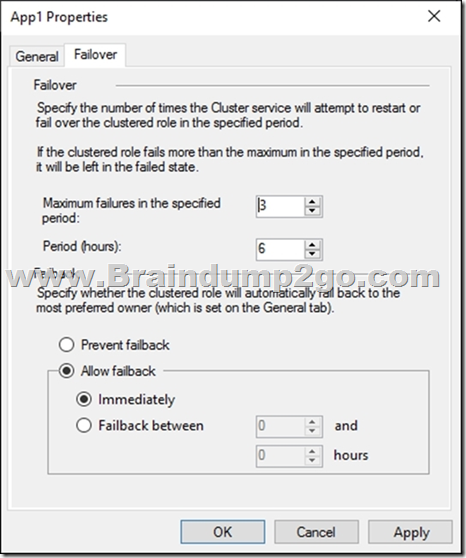
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: From the General settings, you increase the priority of Server2 in the Preferred Owners list.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
Instead, from the Failover settings, you select Prevent failback
Note: The Prevent failback setting will prevent the cluster failing back to Server1.
Preventing failback.
A third potential setting is used after a resource’s cluster node comes back online after a failover. Under the Failover tab is the Failback setting with the default setting “prevent failback.” When failback is configured, the virtual machine will return back to its original host when that host is again available. If you want virtual machines to return to your known configuration after a host problem, this can be a good thing.
Reference:
https://www.computerweekly.com/tip/Configuring-cluster-failover-settings-for-Hyper-V-virtual-machines
QUESTION 107
You deploy Azure Migrate to an on-premises network.
You have an on-premises physical server named Server1 that runs Windows Server and has the following configuration.
* Operating system disk 600 GB
* Data disic 3 TB
* NIC Teaming: Enabled
* Mobility service: installed
* Windows Firewall: Enabled
* Microsoft Defender Antivirus: Enabled
You need to ensure that you can use Azure Migrate to migrate Server1.
Solution: You disable NIC Teaming on Server1.
Does this meet the goal?
A. Yes
B. No
Answer: B
QUESTION 108
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains a single-domain Active Directory Domain Services (AD DS) forest named contoso.com. The functional level of the forest is Windows Server 2012 R2. All domain controllers run Windows Server 2012 R2.
Sysvol replicates by using the File Replication Service (FRS).
You plan to replace the existing domain controllers with new domain controllers that will run Windows Server 2022.
You need to ensure that you can add the first domain controller that runs Windows Server 2022.
Solution; You raise the domain and forest functional levels.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
Instead migrate sysvol from FRS to Distributed File System (DFS) Replication.
Note: Do I need to change SYSVOL replication from FRS to DFS? If your domain is built based on Windows server 2008 or Windows Server 2008 R2, you are already using DFS for SYSVOL replication. If you originally migrated from Windows server 2003, it’s more likely you are still using FRS. In that case, before migration, you need to change the SYSVOL replication method from FRS to DFS.
Reference:
https://www.rebeladmin.com/2021/09/step-by-step-guide-active-directory-migration-from-windows-server-2008-r2-to-windows-server-2022/
QUESTION 109
Your company uses Storage Spaces Direct.
You need to view the available storage in a Storage Space Direct storage pool.
What should you use?
A. File Server Resource Manager (FSRM)
B. the Get-StorageSubsystem cmdlet
C. Disk Management
D. Windows Admin Center
Answer: D
QUESTION 110
You have an on-premises server named Served that runs Windows Server.
You have an Azure subscription.
You plan to back up the files and folders on Server1 to Azure by using Azure Backup.
You need to define how long the backups will be retained.
What should you use to configure the retention?
A. Backup center
B. Windows Server Backup
C. the Microsoft Azure Recovery Services (MARS) agent
D. a Recovery Services vault
Answer: B
QUESTION 111
You have an Azure subscription. The subscription contains a virtual machine named VM1 that runs Windows Server.
The subscription contains the storage accounts shown in the following table.
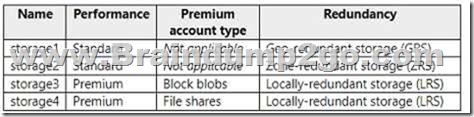
You plan to enable boot diagnostics for VM1.
You need to configure storage for the boot diagnostics logs and snapshots.
Which storage account should you use?
A. storage1
B. storage2
C. storage3
Answer: C
QUESTION 112
Drag and Drop Question
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains a failover cluster named Cluster1.
You need to configure Cluster-Aware Updating (CAU) on the cluster by using Windows Admin Center (WAC).
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
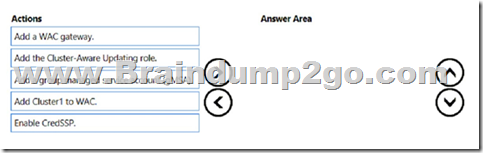
Answer:
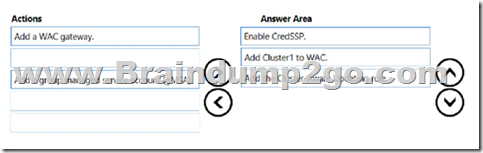
Explanation:
Step 1: Enable CredSSP
Some tasks that require CredSSP to be enabled include:
– Create Cluster wizard workflow
– Active Directory queries or updates
– SQL Server queries or updates
Locating accounts or computers on a different domain or non-domain joined environment
The Credential Security Support Provider protocol (CredSSP) is a Security Support Provider that is implemented by using the Security Support Provider Interface
(SSPI). CredSSP lets an application delegate the user’s credentials from the client to the target server for remote authentication.
Step 2: Add Cluster1 to WAC
Add the failover cluster to Windows Admin Center
Step 3: Add the Cluster-Aware Updating role.
Enabling self-updating mode.
To enable the self-updating mode, you must add the Cluster-Aware Updating clustered role to the failover cluster.
Incorrect:
* Failover clusters do not support gMSAs. However, services that run on top of the Cluster service can use a gMSA or a sMSA if they are a Windows service, an App pool, a scheduled task, or natively support gMSA or sMSA.
* The Windows Admin Center gateway, when published to DNS and given access through corresponding corporate firewalls, lets you securely connect to, and manage, your servers from anywhere with Microsoft Edge or Google Chrome.
Reference:
https://docs.microsoft.com/en-us/azure-stack/hci/manage/troubleshoot-credssp
https://docs.microsoft.com/en-us/windows-server/manage/windows-admin-center/use/manage-failover-clusters
https://docs.microsoft.com/en-us/windows-server/failover-clustering/cluster-aware-updating
QUESTION 113
Hotspot Question
You have a failover cluster named Cluster1 that contains the nodes shown in the following table.
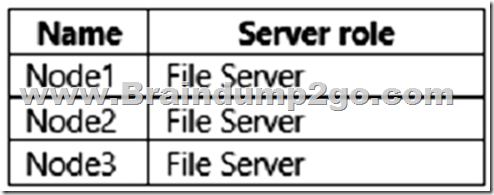
A File Server for general use cluster role named HAFS is configured as shown in the General exhibit.
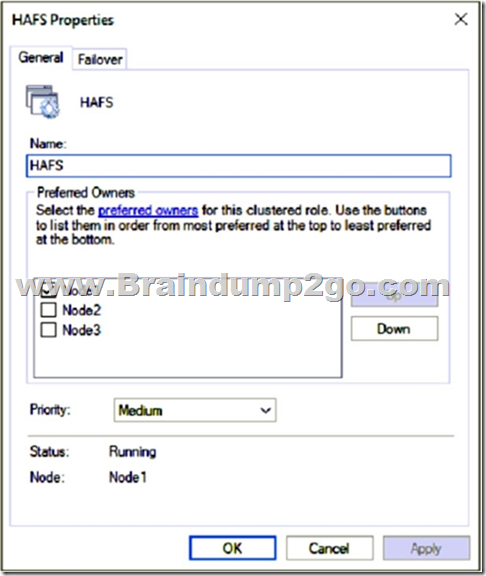
The Advanced Policies settings for HAFS are configured as shown in the Advanced Policies exhibit.
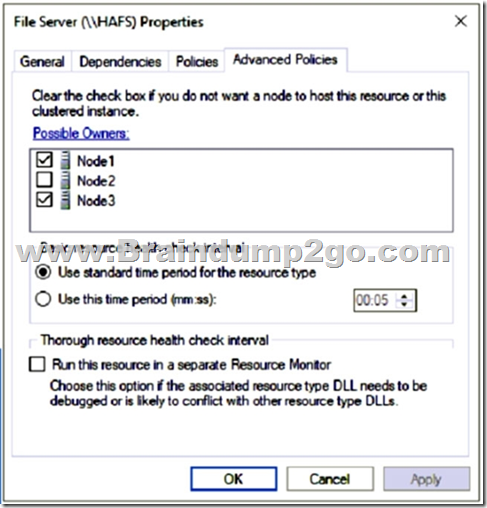
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
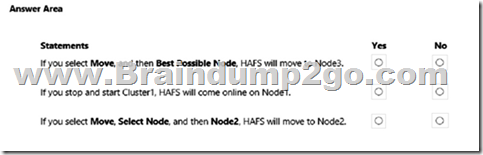
Answer:
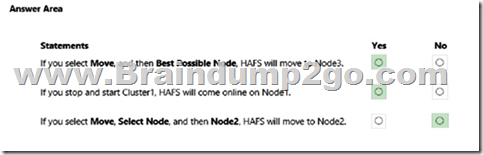
Explanation:
Box 1: Yes
HAFS will move from Node1 to Node3 if we test failover for the cluster.
Note: Test failover.
Test failover of the clustered resource to validate cluster functionality.
Take the following steps:
1. Connect to one of the SQL Server cluster nodes by using RDP.
2. Open Failover Cluster Manager. Select Roles. Notice which node owns the SQL Server FCI role.
3. Right-click the SQL Server FCI role.
4. Select Move, and then select Best Possible Node.
5. Failover Cluster Manager shows the role, and its resources go offline. The resources then move and come back online in the other node.
Box 2: Yes
Node1 is the preferred owner.
Box 3: No
Node2 is not a possible owner of the cluster.
Reference:
https://docs.microsoft.com/en-us/azure/azure-sql/virtual-machines/windows/failover-cluster-instance-vnn-azure-load-balancer-configure
QUESTION 114
Hotspot Question
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains servers that run Windows Server as shown in the following table.
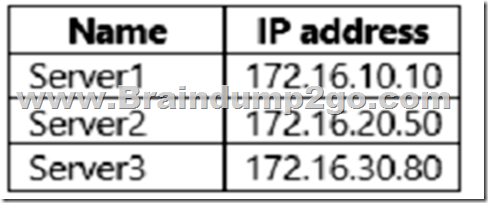
Server1 has the connection security rules shown in the following table.
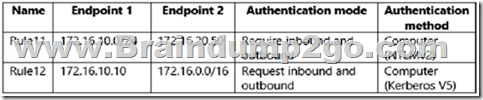
Server2 has the connection security rules shown in the following table.
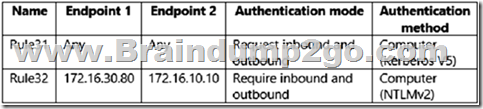
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
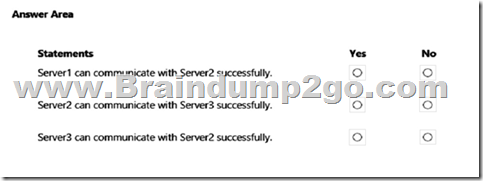
Answer:
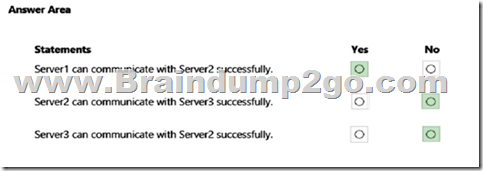
Explanation:
https://learn.microsoft.com/en-us/windows/security/threat-protection/windows-firewall/best-practices-configuring
QUESTION 115
Hotspot Question
You have an Azure Active Directory Domain Services (Azure AD DS) domain named aadds.contoso.com.
You have an Azure virtual network named Vnet1. Vnet1 contains two virtual machines named VM1 and VM2 that run Windows Server. VM1 and VM2 are joined to aadds.contoso.com.
You create a new Azure virtual network named Vnet2. You add a new server named VM3 to Vnet2.
When you attempt to join VM3 to aadds.contoso.com, you get an error message that the domain cannot be found.
You need to ensure that you can join VM3 to aadds.contoso.com.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
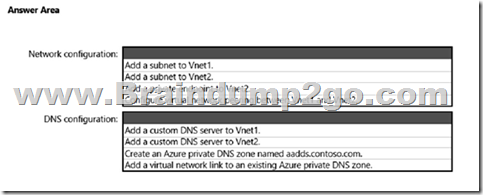
Answer:
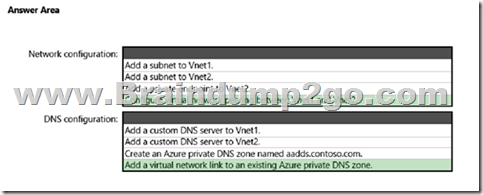
Explanation:
Box 1: Configure virtual network peering between Vnet1 and Vnet2.
Connectivity issues for domain-join.
If the VM can’t find the managed domain, there’s usually a network connection or configuration issue. Review the following troubleshooting steps to locate and resolve the issue:
1. Ensure the VM is connected to the same, or a peered, virtual network as the managed domain. If not, the VM can’t find and connect to the domain in order to join.
If the VM isn’t connected to the same virtual network, confirm that the virtual networking peering or VPN connection is Active or Connected to allow the traffic to flow correctly.
2. Try to ping the domain using the domain name of the managed domain, such as ping aaddscontoso.com.
* If the ping response fails, try to ping the IP addresses for the domain displayed on the overview page in the portal for your managed domain, such as ping 10.0.0.4.
* If you can successfully ping the IP address but not the domain, DNS may be incorrectly configured. Make sure that you’ve configured the managed domain DNS servers for the virtual network.
Box 2: Add a virtual network link to an existing Azure private DNS zone.
The private DNS zone already exists.
After you create a private DNS zone in Azure, you’ll need to link a virtual network to it. Once linked, VMs hosted in that virtual network can access the private DNS zone. Every private DNS zone has a collection of virtual network link child resources. Each one of these resources represents a connection to a virtual network. A virtual network can be linked to private DNS zone as a registration or as a resolution virtual network.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory-domain-services/troubleshoot-domain-join
https://docs.microsoft.com/en-us/azure/dns/private-dns-virtual-network-links
QUESTION 116
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)
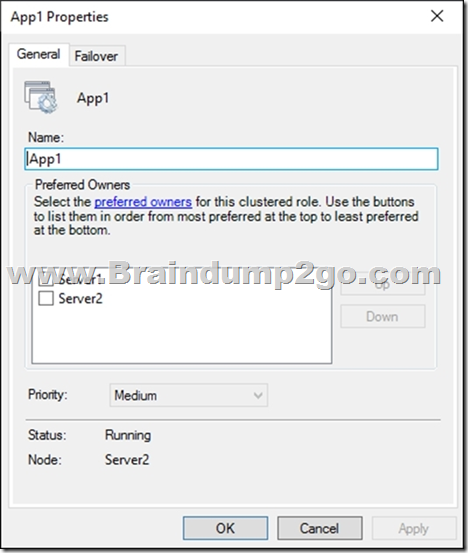
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
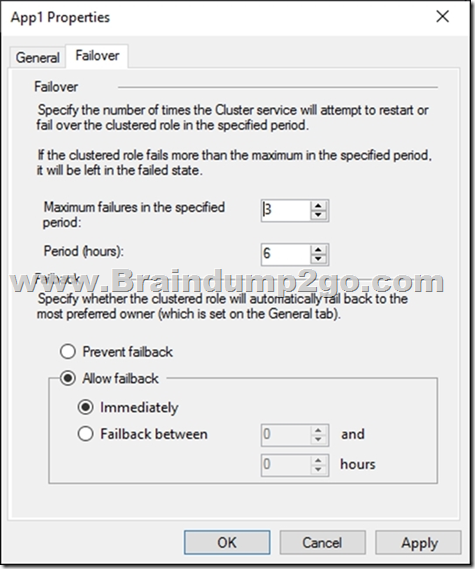
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: You pause the Server1 node in Cluster1 and then start Server1.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
Instead, from the Failover settings, you select Prevent failback
Note: The Prevent failback setting will prevent the cluster failing back to Server1.
Preventing failback.
A third potential setting is used after a resource’s cluster node comes back online after a failover. Under the Failover tab is the Failback setting with the default setting “prevent failback.” When failback is configured, the virtual machine will return back to its original host when that host is again available. If you want virtual machines to return to your known configuration after a host problem, this can be a good thing.
Reference:
https://www.computerweekly.com/tip/Configuring-cluster-failover-settings-for-Hyper-V-virtual-machines
QUESTION 117
Drag and Drop Question
You need to create a Hyper-V hyper-converged cluster that stores virtual machines by using Storage Spaces Owed
Which three actions should you perform in sequence? To answer, move the appropriate anions from the list of actions to the answer area and arrange them in the correct order.
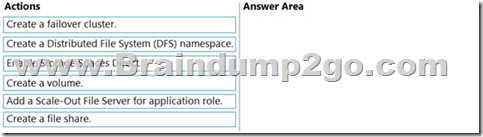
Answer:
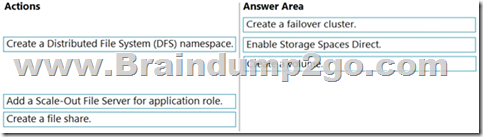
Explanation:
https://docs.microsoft.com/en-us/system-center/vmm/s2d-hyper-converged?view=sc-vmm-2019
QUESTION 118
Hotspot Question
You have the servers shown in the following table.
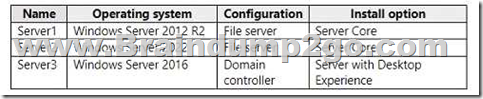
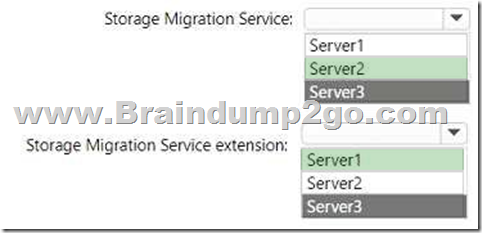
You plan to migrate file shares from Server1 to Server2.
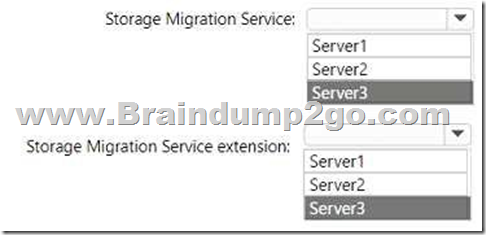
Answer:
QUESTION 119
Drag and Drop Question
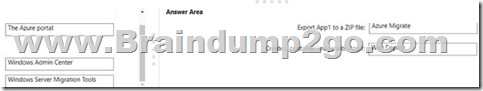
You have an on-premises IIS web server that hosts a web app named App1.
You plan to migrate App1 to a container and run the container in Azure.
You need to perform the following tasks:
– Export App1 to a ZIP file.
– Create a container image based on App1.
The solution must minimize administrative effort.
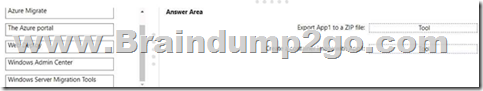
Answer:
QUESTION 120
Which of the following security policies would you configure from the Security Settings extension of the Local Group Policy Editor to control Encrypting File System, Data Protection, and BitLocker Drive Encryption?
A. Account Policies
B. Local Policies
C. Network List Manager Policies
D. Public Key Policies
E. Application Control Policies
Answer: D
Explanation:
Specify the settings for public key policies from Security Settings extension of the Local Group Policy Editor to control Data protection, Encrypting File System, and BitLocker Drive Encryption in addition to specific certificate paths and services settings.
Option A is incorrect. Account policies are defined over devices. They affect how user accounts can interact with the computer system or domain.
Option B is incorrect. These policies are applied to a computer and include policy settings for types like Audit policy and Users Rights Assignments.
Option C is incorrect. Here you need to specify the settings to configure various aspects of how networks are listed and shown on one device or on multiple devices.
Option D is correct. Public key policies are the right policies to configure for the given scenario.
Option E is incorrect. These policies are used to control which groups or users can run specific applications in your organization depending upon the unique identities of files.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/security-policy-settings
QUESTION 121
Being the Windows Server Administrator, you need to review the properties of the Azure AD Kerberos Server to verify that everything is in good order. Which of the following cmdlet would you use?
A. Get-AzADKerberosServer
B. Get-AzureADKerberosServer
C. Retrieve-AzureADKerberosServer
D. Retrieve-AzureADKerberosServer
Answer: B
Explanation:
You can see and verify the newly created Azure AD Kerberos Server with the help of the following command:

This command lists the properties of the Azure AD Kerberos Server which can be reviewed to verify that everything is in good order.
This command lists the properties of the Azure AD Kerberos Server which can be reviewed to verify that everything is in good order.
Option A is incorrect. The right cmdlet to use is Get-AzureADKerberosServer, not Get-AzADKerberosServer.
Option B is correct. Get-AzureADKerberosServer is the command that is used to review the properties of the Azure AD Kerberos Server.
Option C is incorrect. Retrieve-AzureADKerberosServer is not the right cmdlet.
Option D is incorrect. Retrieve-AzureADKerberosServer is not a valid cmdlet.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-security-key-on-premises
QUESTION 122
You have been hired as an expert member to manage the network security of the organization. In a team meeting, you need to present your views on how Windows Defender Firewall can help in addressing the organizational network security challenges. Which of the following statements fit in this context?
A. It will reduce the attack surface of a device, offering an additional layer to the defense-in-depth model
B. When integrated with IPsec, it offers a simple means to enforce authenticated, end-to-end network communications
C. It extends the value of existing investments as it is a host-based firewall that is included with OS, there is no additional software or hardware required
D. All of these
Answer: D
Explanation:
With respect to addressing organizational network security challenges, Windows Defender Firewall provides the following benefits:
– Decreases the risk of network security threats
– Safeguards sensitive data and intellectual property
– Extends the value of existing investments
Option A is incorrect. Not only this statement, but all the given statements rightly describe the benefits offered by Windows Defender Firewall.
Option B is incorrect. The given one is an offering of Windows Defender Firewall, but it’s not the only statement that right describes Windows Defender Firewall.
Option C is incorrect. Not only this statement, but all the given statements rightly describe the benefits offered by Windows Defender Firewall.
Option D is correct. All the given statements describe the benefits of the Windows Defender Firewall that help in addressing the organizational network security challenges.
Reference:
https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-firewall/windows-firewall-with-advanced-security
QUESTION 123
You are an administrator at Contoso and you need to create a new VM with a single OS disk and a single data disk. While creating the VM, you use the default options. You don’t have a key vault set up in your subscription. Which of the following options most accurately define the encryption state of those disks?
A. Both of the disks are unencrypted.
B. Both of the disks are encrypted using server-side encryption.
C. The operating system disk is encrypted using server-side encryption. The data disk is unencrypted.
D. The Data disk is encrypted using server-side encryption. The operating system disk is unencrypted.
Answer: B
Explanation:
Most of the Azure managed disks get encrypted through Azure Storage encryption. It utilizes server-side encryption for protecting the saved data and helping you accomplish the compliance and security allegiance of the organization. It automatically encrypts the data saved on managed disks at rest (data and OS disks) while persisting it to the cloud.
Option A is incorrect. Server-side encryption is enabled by default for new VHDs. With server-side encryption, Azure manages the keys and automatically decrypts data for any read operations without impact on performance.
Option B is correct. All disks are encrypted using server-side encryption by default.
Option C is incorrect. Both OS and data disks are encrypted using server-side encryption.
Option D is incorrect. Both OS and data disks are encrypted using server-side encryption.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-machines/disk-encryption
QUESTION 124
One of the important capabilities of Cluster Shared Volumes (CSV) is the ability to scan and repair volumes online. Which of the following tools can you use to perform the online repair of CSV volumes?
A. chkdsk
B. fsutil
C. Diskpart
D. Diskmgmt.msc
Answer: AB
Explanation:
CSV enabls the users to scan and repair volumes with no downtime when utilizing tools like chkdsk, fsutil, and the Repair-Volume Windows PowerShell cmdlet.
Option A is correct. chkdsk can be used to perform online repair of CSV volumes.
Option B is correct. Fsutil can also be used to perform an online repair of CSV volumes.
Option C is incorrect. Diskpart tool is not used for CSV management.
Option D is incorrect. The Disk Management snap-in doesn’t offer online repair functionality.
Option E is incorrect. Diskpart and diskmgmt.msc are not used for performing the online repair of CSV volumes.
Reference:
https://docs.microsoft.com/en-us/learn/modules/introduction-to-cluster-shared-volumes/2-determine-functionality-cluster-shared-volumes?ns-enrollment-type=LearningPath&ns-enrollment-id=learn.wwl.implement-windows-server-high-availability
QUESTION 125
You want to deploy Storage Spaces Direct on Windows Server. As a part of the process, you have deployed the Windows Server and Configured the network.
Now, the next step is to configure Storage Spaces Direct.
From the below list, choose the sub-steps that are recommended to perform to complete the step.
A. Clean your drives to ensure that the drives are empty
B. Configuring a cluster witness
C. Enabling Storage Spaces Direct
D. Creating the volumes
E. Deploying virtual machines for hyper-converged deployments
F. All of these
Answer: F
Explanation:
To configure Storage Spaces Direct, you need to perform the following steps on a management system that is the same version as the servers being configured. These steps should not be run remotely through a PowerShell session, but instead run them in a local PowerShell session on the management system, with administrative permissions.
The steps are:
1. Clean drives
2. Validate the cluster
3. Create the cluster
4. Configure a cluster witness
5. Enable Storage Spaces Direct
6. Create volumes
7. Optionally enable the CSV cache
8. Deploy virtual machines for hyper-converged deployments
Option A is incorrect. Cleaning the drives is the first and foremost step to configure Storage Spaces Direct.
Option B is incorrect. Configuring the cluster witness is also an important and required step in the process.
Option C is incorrect. Enabling Storage Spaces Direct is the next required step to configuring a cluster witness.
Option D is incorrect. Creating the volumes is an important step but all other steps are also required to configure Storage Spaces Direct.
Option E is incorrect. Deploying virtual machines for hyper-converged deployments is the last step in the process.
Option F is correct. The process of configuring Storage Spaces Direct includes all the above-given steps.
Reference:
https://docs.microsoft.com/en-us/windows-server/storage/storage-spaces/deploy-storage-spaces-direct#step-3-configure-storage-spaces-direct
Resources From:
1.2023 Latest Braindump2go AZ-801 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/az-801.html
2.2023 Latest Braindump2go AZ-801 PDF and AZ-801 VCE Dumps Free Share:
https://drive.google.com/drive/folders/15Sj3aX7fY3gKvLuf_U3ZtIIar43AWvdR?usp=sharing
3.2023 Free Braindump2go AZ-801 Exam Questions Download:
https://www.braindump2go.com/free-online-pdf/AZ-801-PDF-Dumps(89-125).pdf
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!